Recently I wrote a blog post about the usage and implementation of Azure Bastion. Yesterday (19-11) Microsoft offers support to connect to via Azure Bastion with the native SSH and RDP client.
This feature requires to have a Standard SKU for your Bastion host. It lets you connect through by using Azure CLI and expands your sign-in options to include a local SSH key pair and Azure Active Directory.
According to this Microsoft article this feature has the following limitations:
- Native client support is not yet available for use from your local Linux workstation. If you are connecting to your target VM from a Linux workstation, please use the Azure portal experience.
- Signing in to your target VM using a custom port or protocol is not yet available with native client support. If you want to use a custom port or protocol to sign in to your target VM via Bastion, use the Azure portal experience.
- Signing in using a local username and password to your target VM is not yet supported. If you want to use local username and password credentials to sign into your target VM via Bastion use the Azure portal experience.
- Signing in using an SSH private key stored in Azure Key Vault is not supported with this feature. Download your private key to a file on your local machine before logging into your Linux VM using an SSH key pair.
Before you begin you need to have the latest Azure CLI installed.
Configure Azure Bastion
If you already have an Azure Bastion host in use you can simply enable this setting by following these steps:
- Navigate to the existing Bastion host
- Verify that the Azure Bastion host uses the Standard tier/SKU
- Check the Native client support (preview) box and click Apply

Connect to the virtual machine
- Sign into your Azure account and select your subscription containing your Bastion resource.
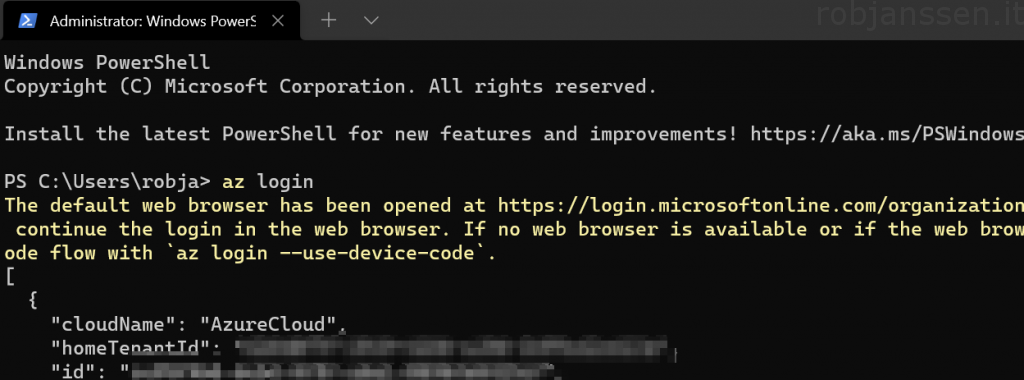
az login
az account list
az account set --subscription "<subscription ID>"Connect to a Linux VM (SSH)
There are 2 options to connect via SSH, 1 is via an Azure Active Directory login, and the other is via a SSH key pair.
- Login via Azure Activity Directory login:
az network bastion ssh --name "<BastionName>" --resource-group "<ResourceGroupName>" --target-resource-id "<VMResourceId>" --auth-type "AAD"
- Login via SSH key pair:
az network bastion ssh "<BastionName>" --resource-group "<ResourceGroupName>" --target-resource-id "<VMResourceId>" --auth-type "ssh-key" --username "<Username>" --ssh-key "<Filepath>"
Connect to a Windows VM (RDP)
Login via the Azure Active Directory login (local account is not supported yet)
az network bastion rdp --name "<BastionName>" --resource-group "<ResourceGroupName>" --target-resource-id "<VMResourceId>"
Once you login with the Azure CLI cmdlet from above the native RDP (like mstsc) will open on your workstation.
Let’s try that
I will demonstrate connecting to an Windows VM via the native RDP client via the Azure Bastion host.
- Enter az login – a browser will pop-up to sign in into the Azure portal (via MFA)
- Use az account set –subscription <subscription ID> to switch to the right subscription
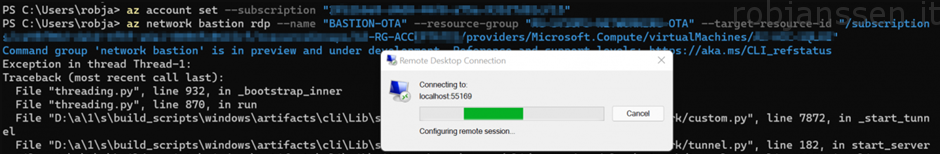
Although I have used the –resource-port “3389” as an additional parameter it still is not connecting. I guess that’s why it is in public preview :).
