It is not a new feature in Azure. Azure Bastion became general available in february 2020. I have used it with other customers, but the implementation was new for me.
In general, Azure Bastion makes it possible to connect to Virtual Machines via the browser over an TLS/443 secure connection. Public-facing VMs are vulnerable and in potential dangerous for your environment. With the usage of Azure Bastion, your VM does not need an public IP or such thing. Azure Bastion is in between that.
The integration is basically being facilitated via the Azure portal. The user/administrator logs in on the Azure portal via an multi-factor authentication. Within the Azure portal simply browse to the VM, click on connect and the secure RDP or SSH connection is being set-up for you. No agent needed, all in native HTML5.

Azure Bastion is a fully, by Azure managed service. It is by-default an hardened black-box which provides you the most secure solution. Azure Bastion lives in a seperate vnet/subnet. Via vnet peering you can control the usage of Bastion for seperate vnets. The steps to implement Azure Bastion are pretty easy:
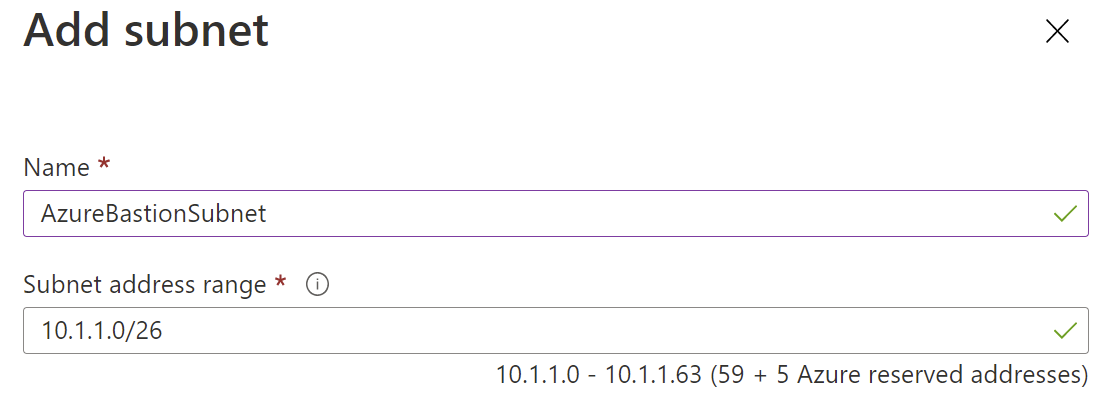
- Create a new virtual network for Azure Bastion
- Within that virtual network create a new subnet which has to be named “AzureBastionSubnet” with a subnet mask /26 or larger.
- Type Bastion into search bar
- Under services, click Bastions
- On the Bastions page, click + Create to open the Create a Bastion page.
- On the Create a Bastion page, configure the new Bastion resource (subscription, resource group, instance name, region, tier, instance count, virtual network, subnet and public IP)
- When that’s all done maybe you want to create a VNET peering in order to manage a VM outside the Bastion vnet
- When that’s also done, you can connect to a VM via Bastion:
- Within the Azure portal, navigate to the VM you want to connect to. Click Connect then select Bastion
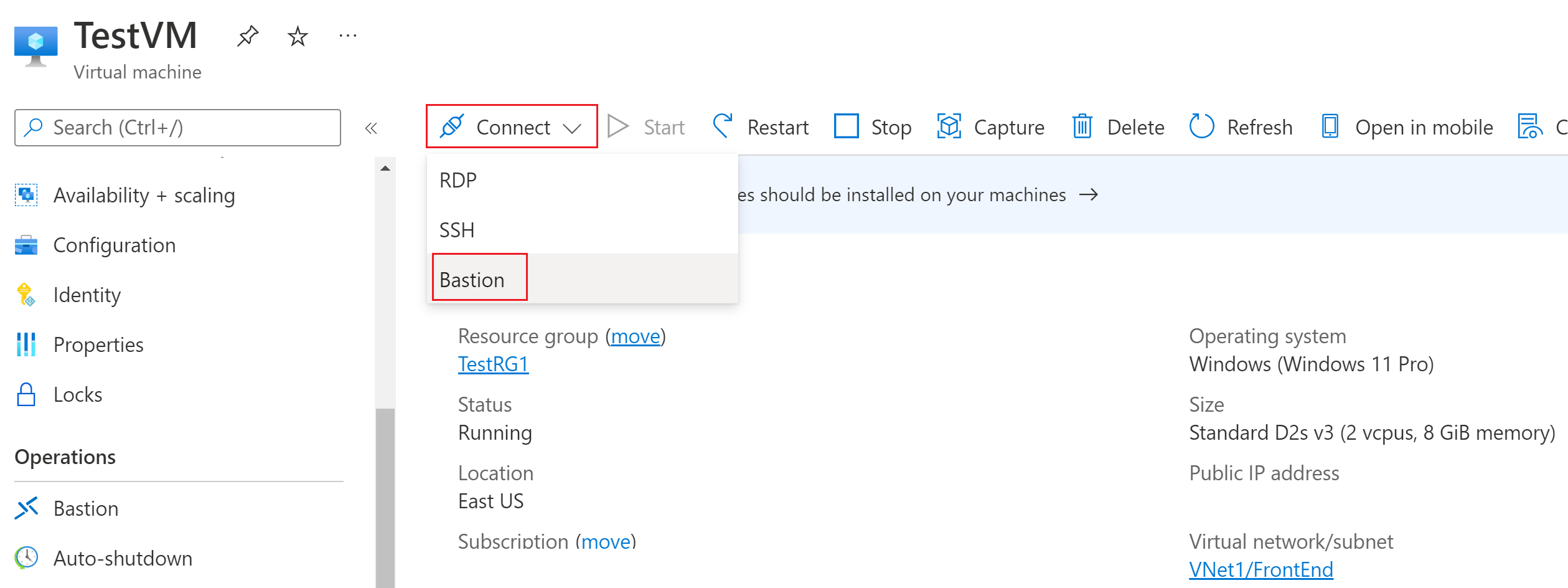
- Click Use Bastion
- Enter your credentials and click Connect
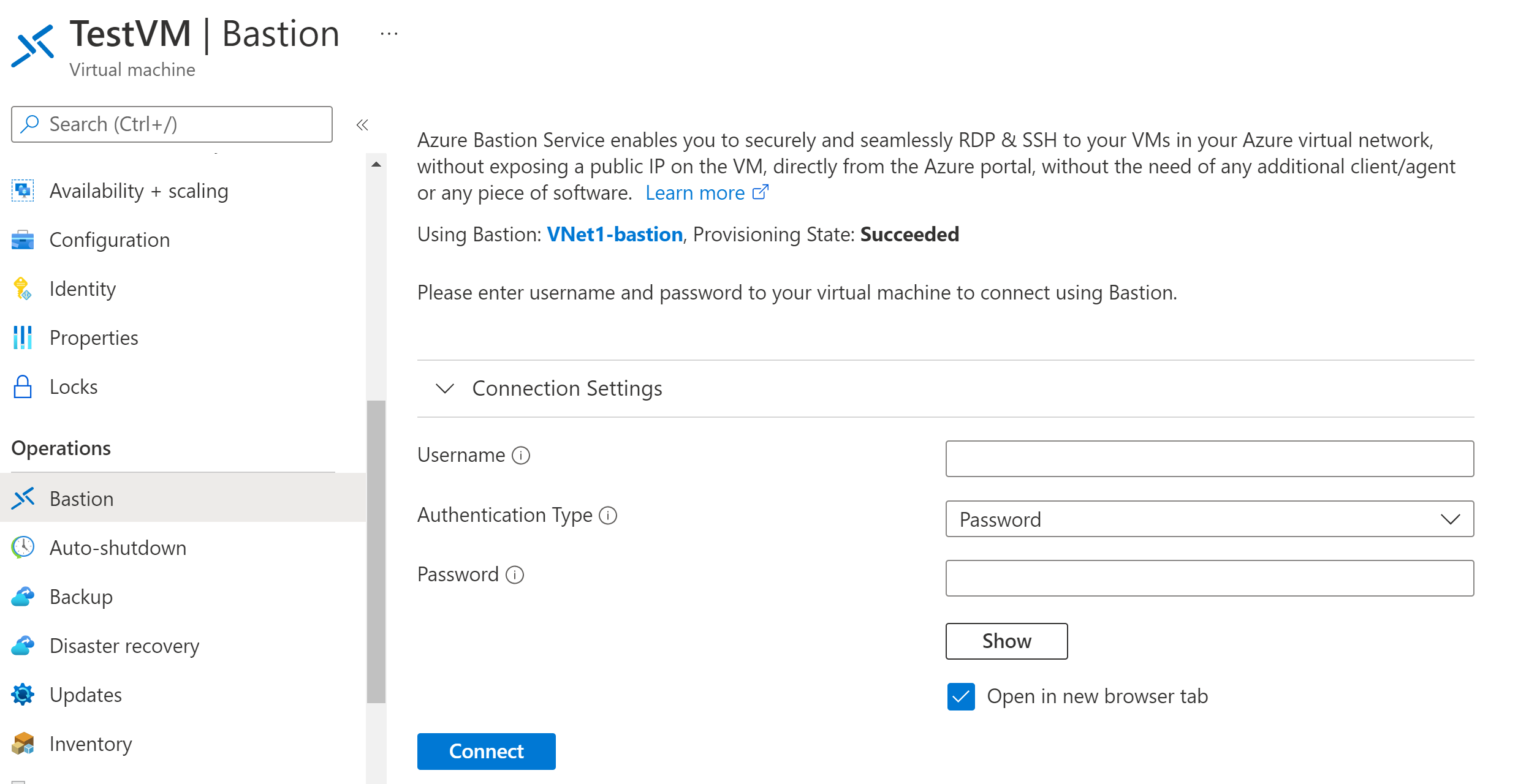
The RDP connection will open directly in a new window in your browser (via HTML5). It makes use of the 443 port & the Bastion service.
You can use keyboard shortcuts for RDP (CTRL + ALT + END) for example. You can also use the clipboard functionality which is built-in. The end-user only needs “reader” rights on the VM objects (NIC, VM & disk) to make use of Azure Bastion.
After you have tested the Azure Bastion functionality you can safely remove your vulnerable public IP ;).

One Reply to “Azure Bastion – secure connectivity to your VMs”