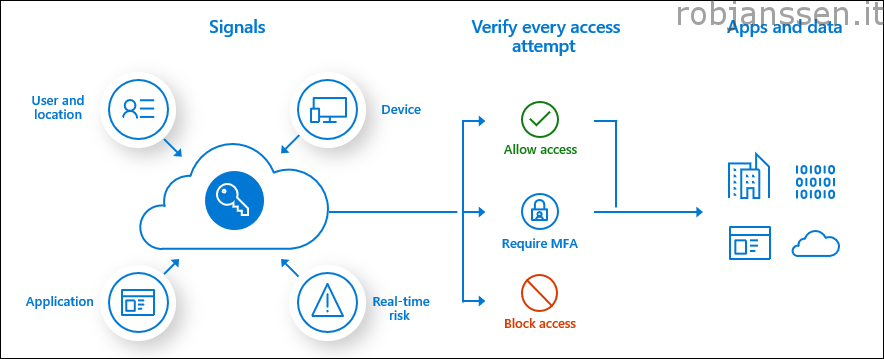
The nice thing about Azure Virtual Desktop is that once you subscribe to an AVD environment, you logon and pass the MFA policy you can choose the “Remember me” option. This option is great for end-users because they don’t need to reenter their username/password.
“Remember me” is fantastic, but not from a security perspective. It is less secure. To protect your users and the environment you want to make sure that the client keeps asking for credentials more frequently. Therefore you can use a separate conditional access policy so that multi-factor authentication will be forced and asked more frequently.
Create and apply the Conditional access policy
- Within the search bar (top of the Azure portal) type in: “Conditional access”. And open Azure AD Conditional Access.
- In the policies overview, click New policy
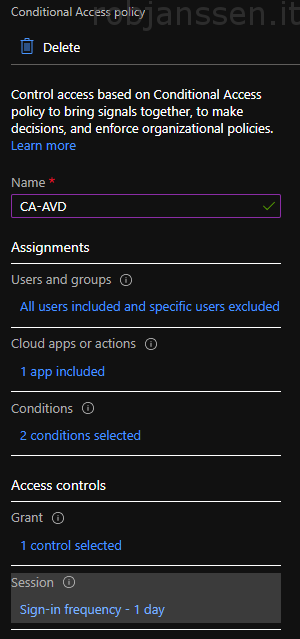
- Type in your desired name, in my case I used “CA-AVD”
- In the Assignments block click on “0 users and groups selected”. And select All users
- Within the “Cloud apps or actions” section click on “no cloud apps….”. Select Select apps. From the list type in “Windows Virtual Desktop” and choose the one starting with “9cdead84-a8ff ……. “
- Click on Conditions within the Client Apps section select Browser & Mobile apps and desktop clients under the modern authentication clients section and click done. Also configure “Locations” for instance if you find that necessary. For example you can disable MFA at trusted locations.
- Under Grant click Require multi-factor authentication and select “Require on of the selected controls” and click Select.
- Within the Session part you can configure to have these control under a time-limit or other session control. In my case I have a sign-in frequency of 1 day. So every day users need to reenter username/password or mfa token.
- Move the Enable policy button to On and click Create
That’s basically it. Be careful to select the right cloud app. If you’re using Azure Virtual Desktop (classic), choose these apps:
Azure Virtual Desktop (App ID 5a0aa725-4958-4b0c-80a9-34562e23f3b7)
Azure Virtual Desktop Client (App ID fa4345a4-a730-4230-84a8-7d9651b86739), which will let you set policies on the web client.
If you’re using Azure Virtual Desktop, choose this app instead:
Azure Virtual Desktop (App ID 9cdead84-a844-4324-93f2-b2e6bb768d07)
Don’t select the app called Azure Virtual Desktop Azure Resource Manager Provider (50e95039-b200-4007-bc97-8d5790743a63). This app is only used for retrieving the user feed and shouldn’t have multifactor authentication.